Has iCloud Been Hacked Again? The Simple Thing to Prevent It
A second round of nude celebrity photos has leaked, and this time the targets include Kim Kardashian, Gabrielle Union, and Rihanna, among others. Over Labor Day weekend, the first set of hacked nude photos from stars like Jennifer Lawrence, Kirsten Dunst, and Kate Upton spread across the web. Many people, including the celebrities themselves, have blamed security flaws in Apple's iCloud system for letting hackers access the images.
Thank you iCloud
— Kirsten Dunst (@kirstendunst) September 1, 2014
There has been no confirmation that Apple was to blame, but the company said it was "actively investigating" the violation of its iCloud accounts. And some security experts believe the leaks could have been prevented if the iCloud's two-factor authentication had been turned on. Apple beefed up its security as a response to the renewed concern.
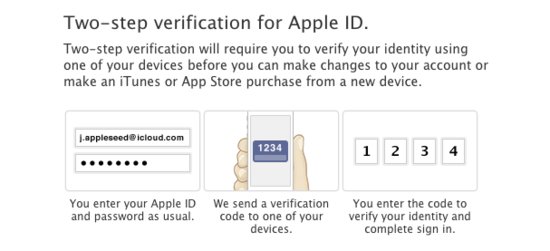
Earlier this year, in March, Apple added the two-step verification for all Apple ID and iCloud users. The security feature prompts users to enter their Apple username and password, plus an additional verification code sent via text message to one of their devices.
:upscale()/2014/09/02/771/n/1922507/b803aa645f00e3db_Screen_Shot_2014-09-02_at_10.29.44_AM.png)
You can enable two-step verification by signing in with your Apple ID at appleid.apple.com. Then go to Password and Security, and follow the instructions at the top of the page.
As evidenced by the nude photo leak, setting up extra measures to protect your information is of the utmost importance in today's increasingly digital age. When iCloud was introduced in 2011, we loved that the cloud-based service provided a free storage and syncing solution for our Apple devices. But with so much of our data automatically uploaded to the web, the service makes all of us — not just celebrities — more vulnerable to privacy predators.
At a 2013 MacWorld session on how to toughen smartphone security, Jacqui Cheng, former senior Apple editor at Ars Technica, told a frightening tale of how her friend, after breaking up with his partner of 20 years, was stalked — and how iPhone location data, accessed through iCloud, made it possible. After her friend's traumatic experience with his ex, Jacqui investigated exactly how iCloud could put your privacy in danger and offered these safety tips for all iCloud users in light of this recent hacking.
First, Change Your Passwords
- To make sure you're not at risk for any security issues, change your Apple ID immediately, as well as your iTunes ID (if it's different). This is the key to your iCloud, which can control almost everything in your device: from your contacts to your photostream to your email.
- Additionally, make sure your password recovery question is info that only you know, and not something a hacker could look up online, such as your mother's maiden name.
Second, Understand How Apps Interact With iCloud
- Find My iPhone — iCloud provides no privacy controls for Find My iPhone because it's designed for your personal use if your iPhone is misplaced. Once someone has your Apple ID info, he or she can find the location of your iPhone and, by proxy, you. This feature is installed by default with iOS 5 and 6 but needs to be enabled through Settings. You can find out when someone is tracking your iPhone from another device by going to Settings > Location Services > Find My iPhone > Turning "Status Bar Icon" to on.
- Find My Friends — While this free app must be installed on a phone to be activated, consider this: if someone finds your phone, unlocked, then he or she can download Find My Friends, have it run in the background, and prevent you from deleting it by setting a parental control passcode (which is different from the lock screen passcode). Notifications can be set up to alert users when "friends" enter or leave locations, like airports, places of work, home, or points of interest. In Settings > Location Services, you can check to see if Find My Friends has access.
- Photostream — Photostream automatically uploads images from a phone's camera roll to the web. Implicitly, a photostream could reveal who you're with and where you are through location markers in photos, like subway stops or monuments. There is also widely available software that reveals encoded GPS coordinates (geotags) from any image taken on your phone. If Location Services are turned on for your Camera, then this location data is readily available to anyone on the web, even if you don't post it on a social network and explicitly state your location.
- iMessage — If your iMessage is associated with an email account (which is most likely if you've synced iMessage to an iPad or Mac), then these messages are accessible to anyone who can download the Messages app. That email account is most likely your Apple ID, and again, if a hacker has that information, then he or she can read every iMessage you send, remotely, on another device without your knowledge.
- Location Services — On your iPhone, go to Settings > Location Services and look at all the apps that use geo tracking. Some of these apps can track you even if it is running in the background, and a lot of apps are reporting your location back to servers. Savvy digital thieves can hack your phone to send that data to an email address or a remote server. If you're at risk, then think hard about what apps really need location services.